Hat tip to @coordinated, who spurred me into writing this macro with his post for 1P v8.
I wasn't going to bother posting this -- hopefully any 1Password users here are happily using version 8. But if anyone is restricted to v7 because they can't update to Catalina for some reason, they might find this useful.
And it combines KM with an interactive Terminal session -- so if you ever need to do that there might be something here for you!
The 1Password CLI 2 page is at https://developer.1password.com/docs/cli/get-started/ -- v2 works fine with 1Pass v7. Like @coordinated I used the manual method, and the whole install and setup only took a minute.
It isn't as featured as @coordinated's macro because I have a limited set of requirements -- get either a username, a password, or both for a 1Pass item specified by ID (not name -- we use a Shared Vault and I can't rely on my co-workers not changing names to "something more sensible"...), across all Vaults. But it would be easy to add @coordinated's extras to this.
Easiest way to get the UUID of an item is to "Share" -> "Copy Private Link" and look at the text, which "="-delimited. UUID is the last but one item:
https://start.1password.com/open/i?a=noIdeaWhatThisIs=vault_identifier=UUID_Is_This_Bit=signin_address
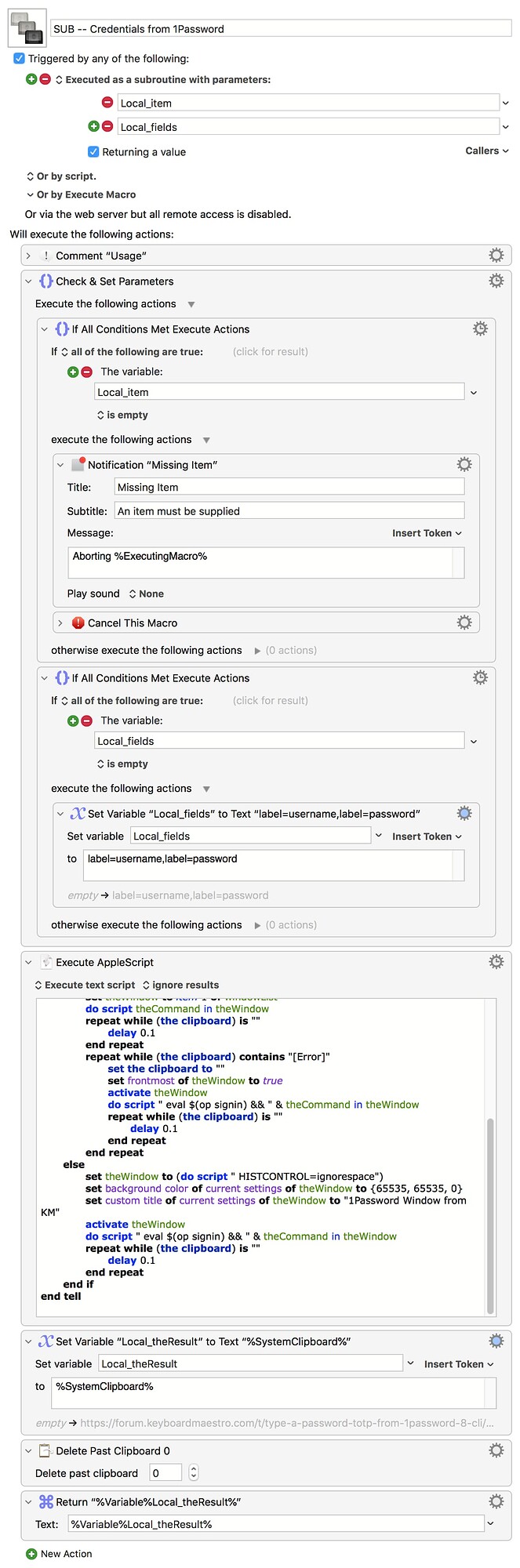
It's a subroutine so it can be called from other macros -- if you do add extras you might need to update the parameters to suit.
SUB -- Credentials from 1Password.kmmacros (8.4 KB)
The meat's in the AppleScript, which either brings the previously-used Terminal window to the front or makes a new one and sets its background to a really lary colour to get your attention. Setting the HISTCONTROL environment variable stops the shell storing any command that starts with a space in the history file, so people can't up-arrow and see (or edit and re-run!) a previous credentials request. The shell scripts themselves are straight forward -- signing in and getting the required fields for the UUID we're interested in -- except that we also redirect errors to standard output, put output on the clipboard, and clear the window so prying eyes see nothing...
The other trick is that the Terminal runs asynchronously to the script so we have to pause and wait until the Terminal command puts something on the clipboard -- so we blank the clipboard and run a looped delay until it's no longer empty. Pop the clipboard into a local variable, delete the past clipboard (again, security), and pass the result back to the calling macro.
I decided to use JSON for the result, mainly so I could error-check in the calling macro -- does JSON length match expected number of parameters, etc.
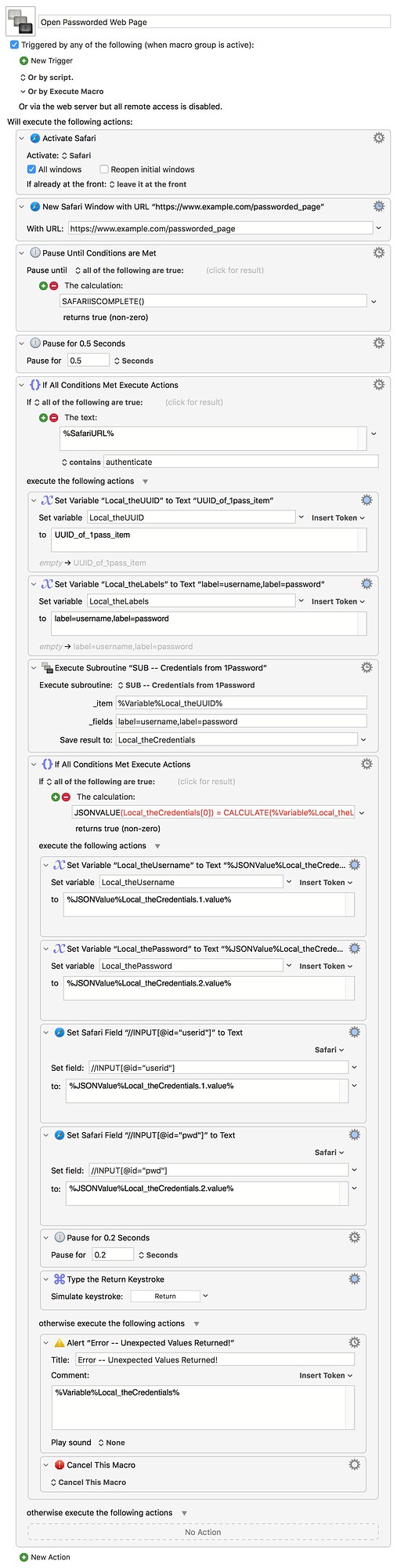
Example calling macro:
Open Passworded Web Page.kmmacros (8.8 KB)
Again this is quite specific to me -- there's an extra pause at the beginning because Safari loads the initial page (so SAFARIISCOMPLETE() is true) then gets bounced to an SSO page with "authenticate" in the URL if I'm not already logged in by previously-set cookies. But all is obvious, and all is easily changed to suit anyone's needs.
It works, but could stand improvement -- particularly in the JSON-handling, which is all new to me. But for all its (and my!) flaws, perhaps it'll help someone do something similar, just as @coordinated's post inspired this.